Warzone 2 THM
You work as a Tier 1 Security Analyst L1 for a Managed Security Service Provider (MSSP). Again, you're tasked with monitoring network alerts.
Hi, this is Warzone 2, again I will be using Brim, Wireshark, Virus Total, and Network Miner.
Q1: What was the alert signature for A Network Trojan was Detected?
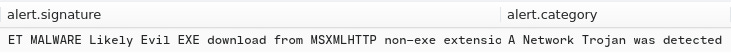
I put the .pcap in Brim, and searched by “A Network Trojan was Detected”.
I saw the alert signature is “ET MALWARE Likely Evil EXE download from MSXMLHTTP non-exe extension M2”
A: ET MALWARE Likely Evil EXE download from MSXMLHTTP non-exe extension M2
Q2: What was the alert signature for Potential Corporate Privacy Violation?
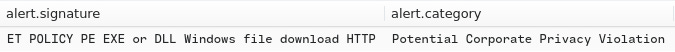
I did the same thing as q1, and searched by the category, which gave us ET POLICY PE EXE or DLL Windows file download HTTP.
A: ET POLICY PE EXE or DLL Windows file download HTTP
Q3:What was the IP to trigger either alert? Enter your answer in a defanged format.
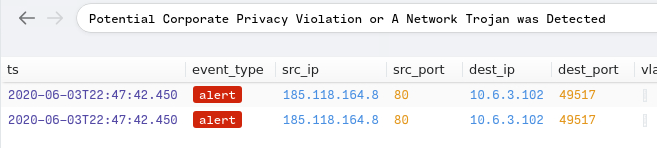
By adding an or statement, I was able to get both alerts to pull up.
I then knew the IP was 185[.]118[.]164[.]8
A: 185[.]118[.]164[.]8
Q4: Provide the full URI for the malicious downloaded file. In your answer, defang the URI.
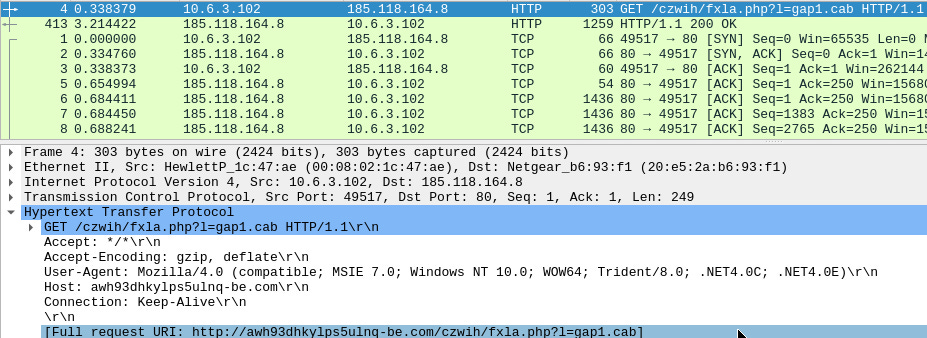
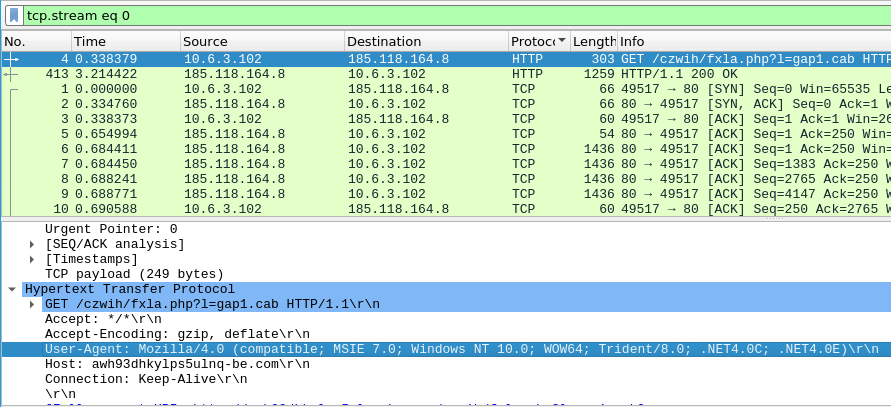
I opened the packets in Wireshark and looked at the get req.
on the bottom you can see the request uri. awh93dhkylps5ulnq-be.com/czwih/fxla.php?l=gap1.cab - I entered that as an answer and it was correct.
A: awh93dhkylps5ulnq-be.com/czwih/fxla.php?l=gap1.cab
Q5: What is the name of the payload within the cab file?
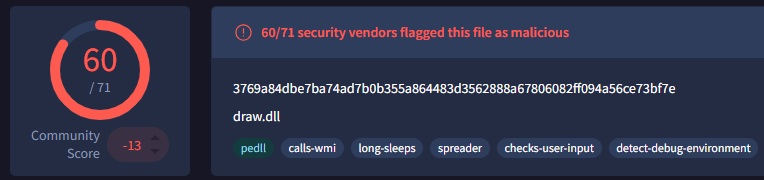
Using Network Miner, I opened the .pcap and found the gap1.cab file. I then put the MD5 hash in virus total to get my answer
A: Draw.dll
Q6: What is the user-agent associated with this network traffic?
back in Wireshark I looked at the get req again and saw the user agent
A: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; WOW64; Trident/8.0; .NET4.0C; .NET4.0E)
Q7: What other domains do you see in the network traffic that are labelled as malicious by VirusTotal? Enter the domains defanged and in alphabetical order. (format: domain[.]zzz,domain[.]zzz)
For this question I had to check a forum, I am not too familiar with VirusTotal and was not really sure where to look. Found the answer to be knockoutlights.com and a-zcorner.com.
A: knockoutlights[.]com, a-zcorner[.]com
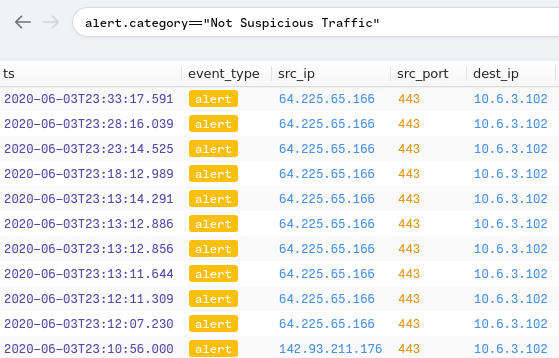
Q8: There are IP addresses flagged as Not Suspicious Traffic. What are the IP addresses? Enter your answer in numerical order and defanged. (format: IPADDR,IPADDR)
in brim I sorted by alert.category=="Not Suspicious Traffic"
A: 64[.]225[.]65[.]166, 142[.]93[.]211[.]176
Q9: For the first IP address flagged as Not Suspicious Traffic. According to VirusTotal, there are several domains associated with this one IP address that was flagged as malicious. What were the domains you spotted in the network traffic associated with this IP address? Enter your answer in a defanged format. Enter your answer in alphabetical order, in a defanged format. (format: domain[.]zzz,domain[.]zzz,etc)
This answer I found using Virus total, just by looking at the Passive DNS replication in relations.
A: safebanktest[.]top, tocsicambar[.]xyz, ulcertification[.]xyz