Warzone 1 THM
You work as a Tier 1 Security Analyst L1 for a Managed Security Service Provider (MSSP). Today you're tasked with monitoring network alerts.
Hi, I will be doing a THM room using Wireshark, Brim, and Virus Total today.
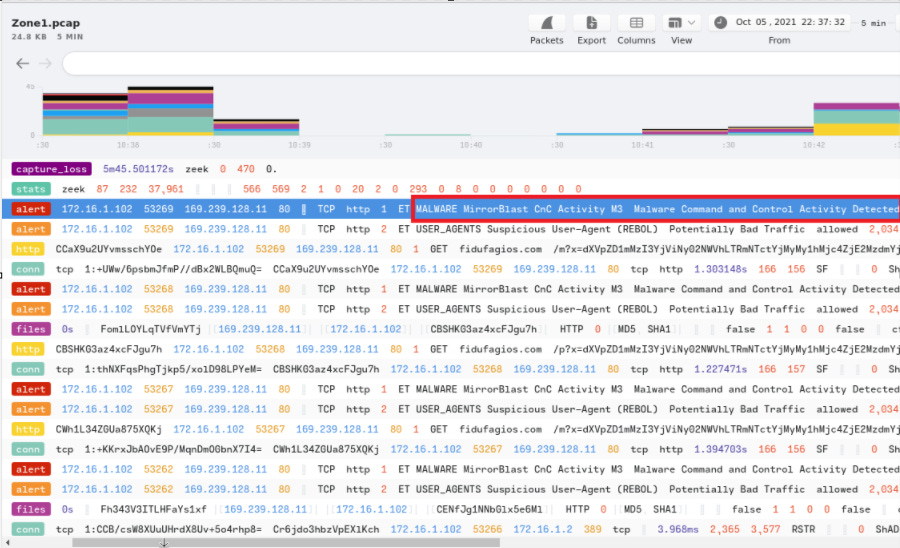
Q1: What was the alert signature for Malware Command and Control Activity Detected?
I put the .pcap in to brim to see the alerts, and we didn’t even have to do any filtering. We were able to see the alert signature we needed right away.
A: ET Malware MirrorBlast CnC Activity M3
Q2: What is the source IP address? Enter your answer in a defanged format. What IP address was the destination IP in the alert? Enter your answer in a defanged format.
These can be seen in the same alert, by hovering over the IP’s I was able to find src and dest.
A: src_ip = 172[.]16[.]1[.]102 dest_ip = 169[.]239[.]128[.]11
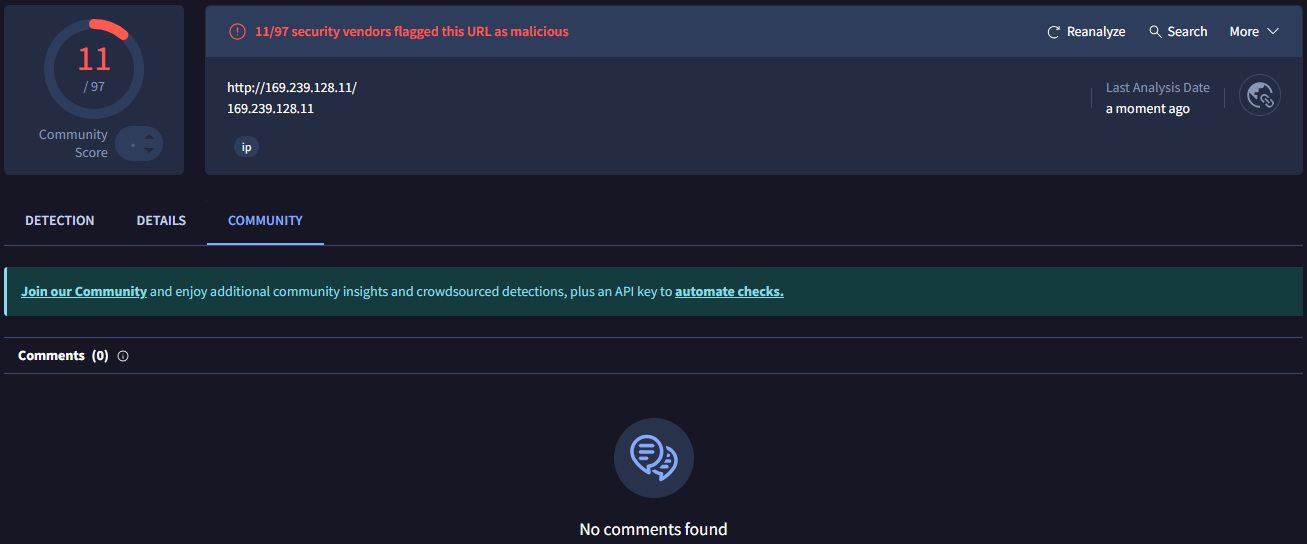
Q3: Still in Virus Total, under Community, what threat group is attributed to this IP address?
I had to check a forum on this question, under community there was nothing showing up for this IP.
A: TA505
Q4: What is the malware family?
This I already saw when initially looking at the alert. Under “alert.metadata.malware_family” we can see that this is “MirrorBlast”.
A: MirrorBlast
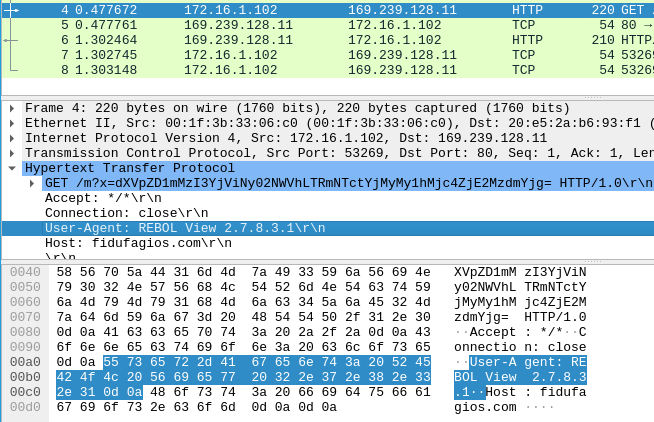
Q5: Inspect the web traffic for the flagged IP address; what is the user-agent in the traffic?
One of the alert signatures shows “USER_AGENTS”, so I opened it in Wireshark to see the related packets. I opened an HTTP get packet and found the user agent to be REBOL View 2.7.8.3.1
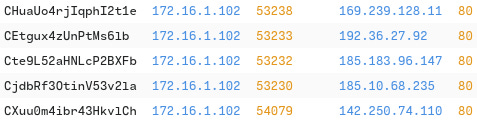
Q6: Retrace the attack; there were multiple IP addresses associated with this attack. What were two other IP addresses? Enter the IP addressed defanged and in numerical order. (format: IPADDR,IPADDR)
Tried using Wireshark to see if our bad IP was talking to any other IP’s ip.addr == 169.239.128.11. This did not turn out with anything. I went back on Brim and sorted by the source IP 172.16.1.102, this also didn’t turn out with anything.
I decided to do only http using 172.16.1.102 _path == "http" and got a couple different IP’s.
From this we can see one is a windows installer, which isn’t really normal. Virus Total confirmed this for me. I also tossed the other IP’s in Virus Total and found our bad IP’s.
A: 185[.]10[.]68[.]235,192[.]36[.]27[.]92
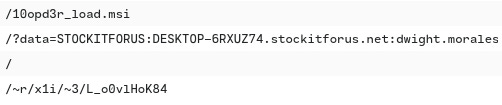
Q7: What were the file names of the downloaded files? Enter the answer in the order to the IP addresses from the previous question. (format: file.xyz,file.xyz)
One of the file names is just given to me: /10opd3r_load.msi. The second one I had to look for. I did see resp_filenames = filter.msi, to confirm this was the answer I queried “file activity” and the filename was filter.msi
A: filter.msi, /10opd3r_load.msi
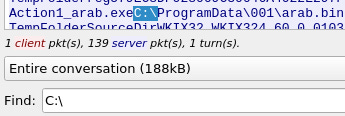
Q8: Inspect the traffic for the first downloaded file from the previous question. Two files will be saved to the same directory. What is the full file path of the directory and the name of the two files? (format: C:\path\file.xyz,C:\path\file.xyz)
I opened the packets and followed the TCP stream of a get request.
I used the format as kind of a hint and used it to filter through the data. The only file path was C:\ProgramData\001\arab.bin so I tried and it worked.
A: C:\ProgramData\001\arab.bin
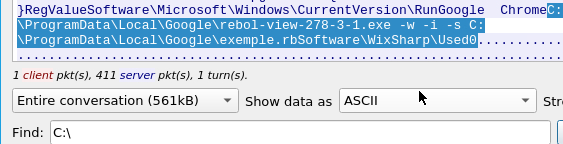
Q9: Now do the same and inspect the traffic from the second downloaded file. Two files will be saved to the same directory. What is the full file path of the directory and the name of the two files? (format: C:\path\file.xyz,C:\path\file.xyz)
I did the same process for this question, and got both answers next to each other.
A: C:\ProgramData\Local\Google\rebol-view-278-3-1.exe,C:\ProgramData\Local\Google\exemple.rb
Thanks for reading :)